I spoke to a few people and realized this could be a good topic for a couple of posts. So without further ado, let’s dispel some myths about cybersecurity careers.
Myth: You don’t need a tech background. Anybody can start a career in cybersecurity. Reality: You need to have an aptitude for computers and/or technology and you need to have an understanding of how computers and applications work and communicate over the network.
This particular article had been in draft for about a month. Apart from being lazy to work through it, there seemed to be too many changes and shifts in the chatbot landscape. Over the past few months I realized there seems to be a fair amount of gaps in understanding of the capabilities of tools like ChatGPT and Bard. News media has obviously caught on to the potential for pushing out subtle scare mongering of the potential dangers of letting AI loose into the world.
We’ve all committed the cardinal sin of hardcoding credentials into code at some point. It’s tempting to take the shortcut and get on with debugging. The changing threat landscape has taught just how critical this failure to comply with security best practices can be. There have been several high-profile cybersecurity incidents that have targeted individuals of an organization to gain credentials to their systems. The LastPass breach post-mortem details the painful experience of the organization losing their DevOps credentials and the trust of the community along with it.
Microsoft Defender for Cloud Apps The Microsoft Defender for Cloud Apps or MDCA offers powerful DLP capabilities as part of it’s CASB offering, especially if your organization owns E5 licenses and uses AzureAD Conditional Access Policies . Previously known as Microsoft for Cloud App Security ior MCAS, this CASB capability works closely with the DLP capability of Microsoft Information Protection to protect data in cloud apps. By bringing the solution under the Defender umbrella of products, all of the settings and policies can now be managed in the Microsoft Security Portal .
(record scratch) You must be wondering how we got here… The Jan 26th OMB memo is historic in directing the US Federal agencies to adopt Zero Trust. Goes without saying that if the US government is adopting the ZT cybersecurity principles, any organization that directly or indirectly deals with the government must follow suite. And everybody else might as well jump on the boat, if not for good cybersecurity, then for good business.
A common misconception about zero trust is that there should be no trust. Rather, the philosophy of zero trust directs us to start with zero implicit trust on an actor, move it through the process of establishing explicit trust until it reaches the required threshold, and perform continuous evaluation thereafter. The difference between imlicit trust and explicit trust in this case being that the attributes of the actor being evaluated are explicilty verified as opposed to being implicitly assumed to be valid.
If we ever needed to jumpstart the move to “Identity-as-a-Perimeter”, COVID-19 certainly made sure it happened. For more than a year most of the global workforce was forced to work remotely and the enterprise had to find creative ways to deliver IT services to the WFH population. If the typical remote access/VPN solution was designed for a 80/20 split between onsite/remote workforce, the ratio was turned on its head overnight. Organizations that planned for the worst-case scenario coped quickly, while those that did not discovered they had to compromise and enable less secure access to enterprise data, sometimes using personal PCs of users on their home network.
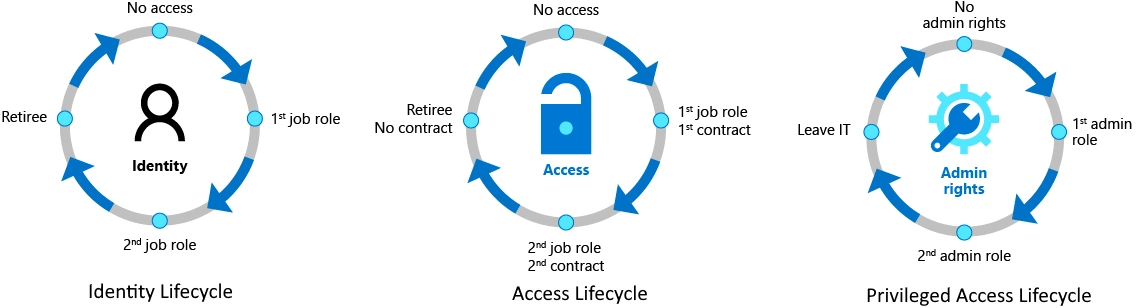
Azure Identity Governance Rebranded as Microsoft Entra Identity Governance , this solution provides a powerful way to manage privilege access lifecycle management. This helps overcome one of the shortcomings of Azure PIM which was that it has no in-built mechanism to request a privileged role. It only provides a mechanism to manage the roles and offloads the task of self-service to other solutions like Id Governance. Before we get in to using Identity Governance, it is important to understand the three liefcycle management concepts as shown below.
Know the enemy and know yourself is perhaps the most well known quote from “Art of War ”. In Cybersecurity a lot of focus is given to the former part of the quote, yet it is an incomplete tactic. It’s a folly to only care about external actors and their TTPs (Tactic, Techniques and Procedures ) yet not know the internal actors. To “know yourself” the cybersecurity team must also understand what the typical network behavior looks like.
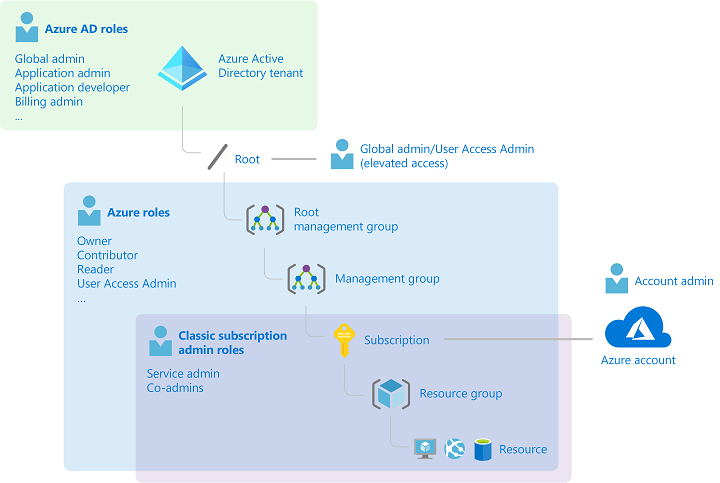
AzureAD Roles vs Azure Roles It’s not quite obvious, but Azure and AzureAD have completely different roles and permissions management mechanisms. Unfortunately, Microsoft not only made the naming convention confusing, but also did a rejig of Azure roles that crerated new roles but left “classic” roles still in place. The diagram below can maybe of a some help, but still requires in-depth understanding of the Azure. AzureAD Roles vs Azure Roles This diagram demonstrates some key differences and relationships between the roles