Using Azure PIM to secure your cloud
How to enable privileged access management for AzureAD and AzureRBAC roles
AzureAD Roles vs Azure Roles
It’s not quite obvious, but Azure and AzureAD have completely different roles and permissions management mechanisms. Unfortunately, Microsoft not only made the naming convention confusing, but also did a rejig of Azure roles that crerated new roles but left “classic” roles still in place. The diagram below can maybe of a some help, but still requires in-depth understanding of the Azure.
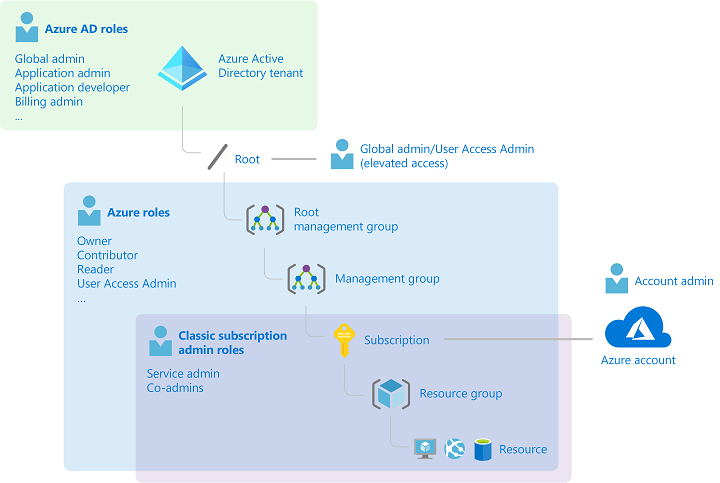
This diagram demonstrates some key differences and relationships between the roles
- AzureAD roles such as Global Admin, Application admin etc are part of AzureAD. There is only one tenant available and therefore the AzureAD roles have a single scope. These roles do not allow you to manage Azure resources nor assign Azure roles except for the case below.
- An AzureAD Global Admin has the ability to elevate privilege to Root and manage ALL management groups and subscriptions tied to a tenant to manage access and grant Azure Roles to users.
- Azure Roles such as Owner, Contributor etc are applicable per Management Group and Subscription. Thus, you maybe an Owner in Subscription X and a Reader in Subscription Y. These roles allow you to manage Azure resources and can also be scoped down to the resource group level. The Owner role allows you to grant Azure Roles to other users. These roles do not allow you to manage AzureAD objects likes users, groups, devices etc or assign AzureAD Roles.
- Azure Roles are hierarchical and users inherit permissions over child resources. So a Subscription level Contributor will inherit Contributor role over all Resource Groups in that subscription, but not vice versa.
If there’s a simple takeaway, then it would be this:
Azure Roles enable management of Azure resources and services like VMs, NSGs etc.
How can Azure PIM (Privileged Identity Management) help
Given that some of these roles are highly privileged, it’s desirable to limit the privileges to users based on the job they need to do and the time they willt ake to complete it. This is also a Zero Trust principle of “Just-in-time” and “Just-enough” access. Azure PIM enables the management of both type of roles along with providing policies that govern the assignment of the roles.
Suggested configurations for PIM managed roles
PIM will enable a role to be either “Eligible” or “Active”. As the name implies, when a user is assigned a role as “Eligible”, they are eligible to activate the roles via the “Activate” button in the PIM interface. When the role is assigned as “Active”, the role remains active on their account. Both of these type of assignments can be timebound. Therefore, a role can be removed from the users after expiry of the timeperiod, or it can be permanently assigned to them in either the “Active” or the “Eligible” state.
Under the Assignment section, the expire after settings indicate when a role assignment should be removed after assignment. You may choose to allow permanent assignment, which would be my recommendation to prevent constant removal of roles.
Similarly, under the Activation section, Activation maximum duration indicates the max amount of a time a user can request for the activation of the role. This only applies for Eligible type of assingment since Active assignments will not have an Activate maximum duration.
It is generally a good idea to keep the top privileged roles for a limited duration. For example, the following table can be a good starting point for configuration of AzureAD roles, assuming roles are permanently assigned.
| AzureAD Role | Type of Assignment | Max Duration of Activation | Comments | MFA for activation |
|---|---|---|---|---|
| Global Administrator | Eligible | 2hrs | Usage of this permission should be rare | Y |
| User Access Administrator | Eligible | 8hrs | Maybe required as full time job for Helpdesk | Y |
| Application Administrator | Eligible | 4hrs | Should only be needed for changes and eployments, but occasional troubleshooting | Y |
| Global Reader | Active | N/A | Low risk role, often required for troubleshooting | N/A |
| Service Support Administrator | Active | N/A | Low risk role, often required for troubleshooting | N/A |
| Owner | Eligible | 2hrs | Usage of this permission should be rare and only for role assingments | Y |
| Contributor | Eligible | 4hrs | Required for deployments and troubleshooting | Y |
| Reader | Active | N/A | Low risk role, often required for troubleshooting | N/A |
Thus, enabling PIM for your tenant and subscriptions would reduce the risk of a compromised account with having privileges for an unchecked duration. The idea being that if your Global Admins are asleep, their accounts should not continue having such privileges. There are still some caveats such as activating multiple roles at once that need to be dealt with, which will be explained in my next blog posts along with the conept of privileged access groups.
Privileged Identity Management enables
* Just-in-time privilege assignment and automated removal of access
* Audit trail of activation of privileged roles
* Enforcement of MFA for elevating privileges
Further reading and viewing:
https://learn.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
https://learn.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-getting-started