Zero Trust
or How I learned to stop worrying and love “perimeterless security”

Zero Trust is a term attributed to Stephen Marsh and mentioned in his ’94 doctoral thesis “Formalising Trust as a Computational Concept” (link to original thesis ). The more than 200 page thesis delves into aspects of defining Trust and it’s relationship to Time, Memory, Optimism vs. Pessimism, Pragmatism vs. Realism and other variables and attempts to arrive at a mathematical definition of Trust. Fortunately for us Cybersecurity practitioners, Zero Trust has since been studied, developed and evolved into a much simpler concept and security architecture. The term was revitalized in 2010 by John Kindervag who also authored the seminal articles published under Forrester (which, though they are locked away behind a paywall on Forrester’s site, are nevertheless still available under other vendor sites here: Introducing Zero Trust Model and The Zero Trust Network Architecture ). These articles may be more than a decade old, but are still foundational and relevant to understanding and adopting ZT Architecture today.
It’s been more than 10 years. Why is ZT a hot topic today?
When the ZT architecture was first proposed, it was hailed as the Holy Grail of cybersecurity architecture (ironically, just as it is being done now). However, I think there were two challenges with adopting ZT at scale.
- Organizations weren’t ready to adopt ZT just yet: I recall a few conversations with some of my leaders at the time and the consensus was we couldn’t adopt the strategy of ZT. And they were right. Had we attempted to enforce ZT concepts on applications and infrastructure, we’d have had to build our own solutions based on existing products and services. The enterprise would not have been able to operate efficiently and security would have been hated even more than they seemed to be at the time. The traditional model of security also seemed to fill the need at the time. Cloud and Saas were still picking up steam, but in most cases did not outnumber the systems that enterprises ran “on-premises”.
- Vendors weren’t ready to interoperate: It would take a few years of development for vendors to incorporate ZT conecpts into their products, but also to make their products modular enough and interoperable enough to integrate with other tools and fit into the ZT architecture. To be honest, this is still an issue, and it’s a very recent development that the Zero Trust Center of Excellence was announced by NIST with participation by leading vendors across domains to overcome this issue.
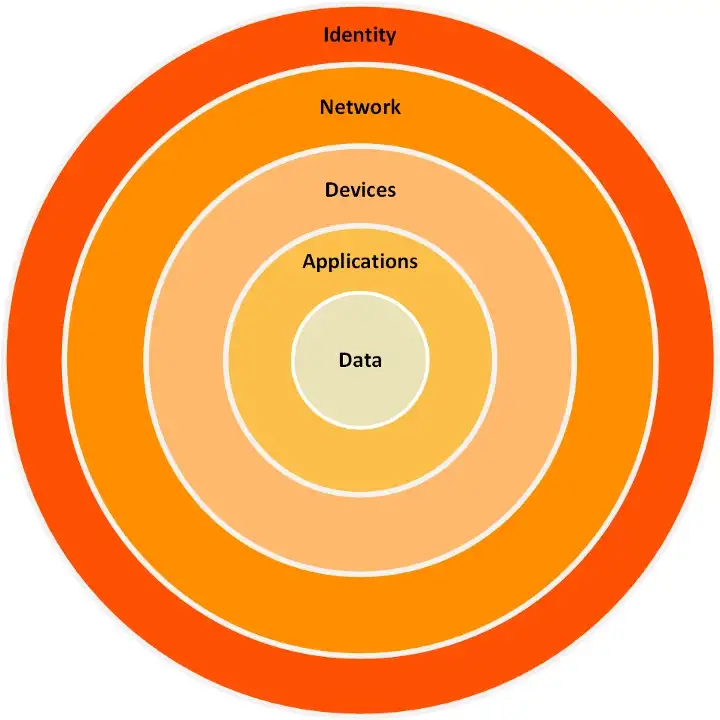
Today, enterprises cannot ignore the efficiencies of running workloads in the cloud or leveraging Saas to optimize IT cost. On-prem and hosted datacenters are quickly becoming expensive and hard to justify. The effect on security because of these shifts are that users can no longer be limited to an on-premises user directory, data can no longer be kept within the company network perimeter and the IoT devices have all but removed the traditional boundaries of the company network perimeter. Add to the fact that in 2020–2021 almost every organization had to learn to enable users to work remotely, often connecting from unsecured, unmanaged network locations to the corporate, the definition of the company perimeter has changed drastically.
The combination of changing business environment, forced adoption of remote work capabilities, and the catalyst of high profile attacks in 2021 by cyber attackers abusing the traditional “trust” within a company network has paved the path for wide adoption of ZT. The US Government’s push to adopt Zero Trust in federal agencies is also bolstering the initiatives towards ZT. And for cybersecurity vendors, it is a ripe time to capture the market, fill the gaps we have always known about and change the mindset of what cybersecurity means. And for cybersecurity practitioners, it’s time to stop worrying about keeping users and data within the perimeter (physical and virtual) and adopt “perimeterless security”.
What’s next for ZT architecture?